Many enterprises in the DoD and US Federal Government are struggling with how to implement inexpensive 802.1x solutions for their wired LANs. Especially in the DoD, there are specific regulations that require the use of 802.1x on the Unclassified Networks (NIPRNet) and Classified Networks (SIPRNet). For your reference, those requirements are called Security and Technical Implementation Guidance (STIG) documents.
DoD 802.1x STIGs
Those STIGs for 802.1x in the DoD are:
- STIG ID: NET-NAC-010: “The IAO will ensure that 802.1x is implemented using a secure EAP such as EAP-TLS, EAP-TTLS or PEAP.”
- STIG ID: SRC-NAC-020: “Ensure remote endpoint policy assessment proceeds only after the endpoint attempting remote access has been identified using an approved method such as 802.1x or EAP tunneled within PPP.”
- SRG-NET-000151: “The network device must authenticate devices before establishing network connections using bidirectional authentication between cryptography-based devices,” and, “The devices typically use either shared known information (e.g., Media Access Control [MAC] or Transmission Control Protocol/Internet Protocol [TCP/IP] addresses) for identification or an organizational authentication solution (e.g., IEEE 802.1x and Extensible Authentication Protocol [EAP], Radius server with EAP Transport Layer Security [TLS] authentication, Kerberos) to identify and authenticate devices on local area networks.”
Why 802.1x?
802.1x is an IEEE standard that enforces switch-port authentication for devices, servers, and workstations to the network. Basically, the device will use an 802.1x supplicant and negotiate the type of authentication using EAP messages. Once the EAP protocol is negotiated, the switch will ask the device for its credentials. The device will provide them using only the following methods:
- EAP-TLS – the most preferred option in the DoD, it provides robust FIPS 140-2 encryption and integrity algorithms. It also provides support for certificate authentication – instead of just user name and password.
- EAP-PEAP – Protected Extensible Authentication Protocol (PEAP) works the same as EAP-TLS except uses a user name and password, vice certificates. TLS is still used for outer channel encryption, and MSCHAPv2 is used for inner-channel authentication (user name and password)
An Inexpensive Solution Using Microsoft Server Roles
Without even researching options, I have found most enterprises (especially in the DoD) will instead purchase commercial solutions to do this instead of simply looking inside of their current offerings. For example, many look at Network Access and Control (NAC) products like:
- Cisco Identity Services Engine (ISE) – this is expensive. I recommend looking elsewhere if you are just looking for 802.1x. If deeper NAC options are required like BYOD, profiling, or the like, then ISE may be good to look into. Otherwise, don’t.
- Juniper Unified Access Control (UAC) – also expensive, provides most of the same functions as Cisco’s ISE.
As for inexpensive and already in use, most DoD/Federal Government enterprises already have and pay for the Microsoft solution. The prerequisites are the following:
- The enterprise must have a healthy Microsoft Active Directory with at least a 2008 Domain Schema
- The enterprise must have deployed an internal Microsoft CA that is domain integrated
- New client certificate templates must be created and installed with auto-enrollment
- The enterprise will need to deploy Microsoft’s Network Policy Server (NPS). NPS is the replacement for Microsoft’s IAS (Internet Authentication Service).
- A layer-2/3 switch with RADIUS and 802.1x authentication support. All modern switches have this support today.
Step 1: Verify Microsoft Certificate Authority
First step is to make sure the CA has a workstation certificate that can be distributed throughout the domain. Permissions for enrollment and auto-enrollment should be given to all domain computers and users. Once this is implemented, test enrollment via a workstation. This process must also be followed for the Microsoft NPS server. It must have an NPS/IAS server certificate.
- Open the MMC as an administrator, add the Certificates template, and check Computer.
- Open the personal certificate store, right-click and click “request new certificate.”
- Confirm it is distributed via Active Directory and click Next.
- If there are any login or permissions errors here, then the users and computers were not given enough permissions on the CA server
- Check the box for the newly created workstation certificate, and click enroll.
- Next, ensure the “Wired AutoConfig” service is started and is automatic.
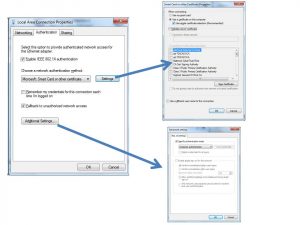
- Ensure the Authentication configuration looks like this (Windows 7):
Step 2: Configure NPS Server
The NPS server is a server role that can be added to any Server 2008, 2008 R2, or 2012 server. Install the role then follow these configuration parameters:
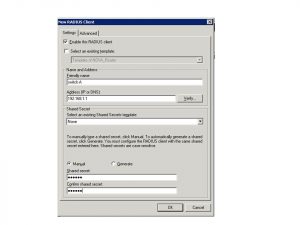
Add the RADIUS clients. These will be the switches that the workstations will connect to. The need to have IPs on them and reachable to the NPS server over RADIUS UDP ports 1645 or 1812.
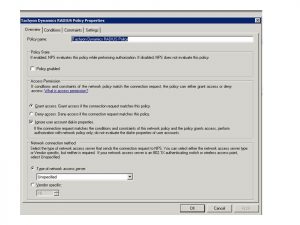
Next, add the Network Policy:
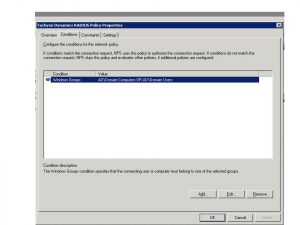
Create the policy to use the Windows Groups “Domain Computers” and “Domain Users”
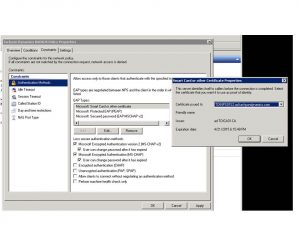
Next, configure the Policy Constraints to use EAP-TLS and PEAP, then select the certificate that the NPS server has.
Restart the NPS service and it will be ready to authenticate computers using their certificate, and users for PEAP.
Step 3: Configure the switch
Lastly, we need to configure the switch to support 802.1x authentication on the port. The following is a config snippet to use for a standard Cisco switch:
! enable the AAA module aaa new-model ! Enable 802.1x for the switch dot1x system-auth-control ! enables the 802.1x service dot1x guest-vlan supplicant ! in case network access should be enabled for limited network access ! Configure 802.1x on the switch port int gix/x switchport access vlan 10 switchport voice vlan 21 ! in case there is a VoIP phone plugged in switchport mode access authentication event fail action authorize vlan 30 ! this is the guest VLAN authentication event server dead action authorize vlan 30 authentication event no-response action authorize vlan 30 authentication port-control auto ! enables authentication on the port authentication periodic ! used to re-authenticate the port every 60 minutes authentication timer inactivity 60 authentication host-mode multi-domain ! used for the VoIP Phone to be able to allow for multiple MAC addresses dot1x pae authenticator ! tells the port to use 802.1x for authentication dot1x timeout server-timeout 50 ! recommended timeouts dot1x timeout tx-period 2 dot1x timeout supp-timeout 5 qos trust device cisco-phone ! in case there is a Cisco VoIP phone spanning-tree bpduguard enable ! spanning-tree best practice spanning-tree portfast ! Spanning-tree best practice no shut ! Add a radius server to use for 802.1x aaa authentication dot1x default group radius ! tells the switch to use RADIUS for 802.1x ip radius source-interface Vlan99 ! this is the network management VLAN radius-server host 192.168.1.2 auth-port 1812 acct-port 1813 key secretkey123 ! Radius server IP address
As you can see above the configuration is very simple. A few things to verify before plugging the workstation in and testing:
- The workstation has a computer certificate issued by the AD CA server
- The workstation has the Wired AutoConfig service started and enabled with the recommended options from above
- The NPS server has the NPS service running with the correct configurations, and it has the NPS/IAS certificate from the CA
- The NPS server has the switch IP address with the correct key in the RADIUS clients section
- The switch has all the necessary configurations from above
Step 4: Troubleshooting
After plugging in the workstation, and there are still problems the best way to troubleshoot is by enabling debugging on the switch:
debug radius all debug dot1x terminal monitor
Also, look to the Windows NPS server logs. If all else fails, use Wireshark on the workstation and filter on “EAPOL.” Use Wireshark on the server and filter by “RADIUS.” You should be sure to see any issues from here.
Of course, if you still have issues or questions, or want to reach out for help or engineering support, go ahead and get in touch with us!